Previously posted here at Grand Stream Dreams:
- Partition and Disk Management: Part I – Dancing with Diskpart
- Partition and Disk Management: Part II – Free and Useful Tools
In “Part I – Dancing with Diskpart” I was working with some Dell systems and in using GParted noted some strange things with the drives that I hadn’t picked up before in using the CLI DiskPart tool.
Note: these were captured pre “clean all” which would have removed the MBR information as well as zeroed out the drives.
I captured a few screenshots for posterity from two different systems.
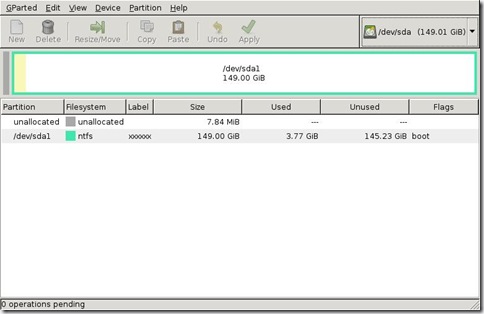
First there was this dual-partitioned system.
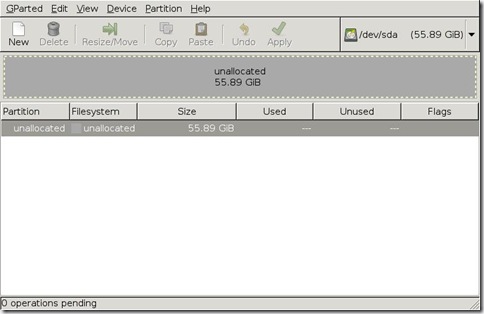
And on this other example system…
Notice in both that “unallocated” 7.84 MiB space at the front?
Yeah, I did as well.
I also had a third laptop system from Dell that also contained that same leader section of unallocated space, the primary partition space, then an additional trailing section of unallocated space about 1 MiB in size.
What I want to see on our desktop and laptop systems is this before I create a single partition on the drive.
Dangerous Space
There are a number of reasons why I don’t like unallocated space. First and foremost it could be a potential hiding place for sophisticated baddies or data.
While the Hartland processor fallout is still being reviewed and understood, these are great posts to familiarize yourself with the danger of unallocated space on a system.
- Don’t let what Happened to Heartland Happen to You– Part One – Ascension Blog
- Don’t let what Happened to Heartland Happen to You - Part Two – Ascension Blog
- Heartland Sniffer Hid In Unallocated Portion Of Disk – StorefrontBacktalk Blog
It’s a sophisticated threat but still one that system administrators (and forensics folks) still need to be aware of. If space is unallocated on a system, stuff can be hidden there. You need to identify it, assess it, and if not required, remove it. It’s not the most common threat or hiding-hole, but still, old-school is becoming popular again in threat vectoring.
Also, we are paying for use of the whole drive, and while it is tiny, that space can’t be used by the user/system. Every bit counts!
Finally, it could conceivably through disk partitioning activity out of whack a bit. So having it all allocated is a good thing.
If someone brings me a (non-whole-disk encrypted) system and I find such unallocated space sitting around, I have a number of techniques to use.
If it is a new system with fast hardware, I will just use GParted to merge the space into the existing partition. Easy and fairly fast.
If it is an older system with slow hardware, I will take an ImageX image of the partition(s) and dump the WIM file to a USB disk. Then I will do a full DiskPart series of commands to blow out the entire drive settings and re-create a single (or two) partition using all the space on the drive. Then after formatting, I will restore the image WIM back to the system.
But what about that “unallocated space” on those Dells?
Yes, what about them.
Dell seems to prep its drives with one or both of these spaces. These really aren’t “unallocated” but specially allocated by Dell for system recovery and diagnostic tool partitions, not normally accessible except from the BIOS.
Here are some posts that might help clear things up with this.
Inside the Dell PC Restore Partition - Dan Goodell’s awesomely detailed exploration and exposition of all things Dell partitions. Turns out there could be up to three separate and distinct Dell specialized partitions you might encounter. The first is the Dell Utility partition which contains diagnostic tools accessible from BIOS. The second could be the “Dell PC Restore by Symantec" utility--colloquially referred to as DSR ("Dell System Restore")” partition. The third might be the Dell MediaDirect Partition which allows some Dell notebooks to boot for some media-enjoyment routines without needing to bring up the full XP OS system. Dan has all the information needed to understand and work with all things Dell partition. It is THE resource on this area.
Delete and Remove to Unlock EISA Hidden Recovery or Diagnostic Partition in Vista - My Digital Life. Being a DiskPart guy, this was good information to know:
- Open a command prompt as administrator.
- Run Diskpart application by typing Diskpart in the command prompt.
- In the “Diskpart” prompt, enter rescan command and press Enter key to re-scan all partitions, volumes and drives available.
- Then type in list disk and press Enter key to show all hard disk drive available.
- Select the disk that contains the partition you want to remove. Normally, with just 1 hard disk, it will be disk 0. So the command will be:
select disk 0
Finish by Enter key.
- Type list partition and press Enter key to show all available and created partition in the disk selected.
- Select the partition that wanted to be deleted by using the following command, followed by Enter key:
select partition x
where x is the number of the EISA based recovery partition to be removed and unlocked its space. Be careful with the number of this partition, as wrong number may get data wipes off.
- Finally, type in delete partition override and press Enter key.
Once the partition has been deleted, exit from Diskpart, and now users can use the much familiar and much easier Disk Management tool in Windows (diskmgmt.msc) to manipulate the freed unallocated partition. Users can create a new volume (partition) with this space, or simply merge it to existing partition by extending the size of the existing partition.
Sometimes you will have to use the “override” argument when you delete a partition so it doesn’t error out due to special flagging.
Partitioning problems - [H]ard|Forum – More DiskPart tips and helps.
Guide: How to Delete Hidden Recovery Partition on Vista - Notebook Forums and Laptop Discussion – Picks up and expands the tip offered by “My Digital Life” noted above Forum threads are usually informative and this one really is.
How to delete Dell Service Partition - UBCD4Win Forums –and HAL: "ACPI Uniprocessor PC" vs. "Advanced Configuration and Power Interface PC"? - arsTechnica Forum. Users come to realize they needed to update the boot.ini file after removing a Dell Service Partition as it changed the volumes listed and used by the boot.ini file. Be aware of this.
Dell Utility Partition Restoration – Great Grand Stream Dreams post (IMHO) that explains how to rebuild the Dell Utility Partition if you regret dumping it (not for the feint of heart), as well as just using a Dell Diagnostics boot CD to accomplish the same thing (much better IMHO).
Removing Dell partition - NotebookForums.com – After all this, I come to find out that some Dell systems have a file under the directory Dell\Utilities\DSR on some hard drives called DSRIRRemv2.exe. Double click on this and then click the OK button to remove the Dell PC Restore partition. However, despite looking on all our Dell systems, CD’s, and the Googles, I have been unable to find and obtain a copy of this file (or DSR folder) to test and find if it is fast or effective.
Important Considerations
A few things to keep in mind before you start whacking away these Dell partitions.
- If you are a PC system noobie or average home user, you probably don’t want to mess with them. They don’t take up that much drive space and may contain critical files needed to restore your system to an operational state if it hard-crashes and you have to OEM system-restore it. If key files there are gone and you don’t have your OEM system restore disks, you are out of luck.
- Advanced or pc-building enthusiasts are probably sophisticated and knowledgeable enough to strike out on their own and dump these “unallocated” spaces. Be careful and know what you are doing.
- Many other OEM laptop and system builders also seem to use similar partitions and structures as Dell does. You might want to take a look to see what is there.
- As a system administrator, we have a lot more tools, resources, and knowledge at our disposal and having these spaces actually presents more of a problem and issue with security and service of systems than it provides benefit for system recovery and diagnostics. We want them cleared and gone. That is probably not a very common scenario for most users.
You have been warned.
Bonus Tip: Taking and Saving a Screenshot in GParted
I’m a screenshot pro.
I’m also pretty good about mounting portable drives in Linux and copying files back and forth.
For some reason this was giving me fits to get those GParted screenshots over to my USB stick.
GPARTED DOCUMENTATION - SAVE_DETAILS – One method
and
GParted forum / Gparted GUI disappears From “cmdr”
1. Run "GPartedLive CD"
2. Take screenshot of "GParted" window
3. Start "Terminal" (by Desktop icon)
4. Attach USB stick, wait until LED flickered.
5. Type (first parameter is a lowercase L)fdisk –l
6. Note device name of logical USB drive, e. g. /dev/sda1
7. Type (replace "sda1" with your USB stick's device name !) and confirm one line after the other.mkdir /mnt/usb
mount /dev/sda1 /mnt/usb
mkdir /mnt/usb/gpdebug
cp /root/gparted.jpeg /mnt/usb/gpdebug/shot1.jpeg8. Repeat last line as often as you need, giving the target file (shot1.jpeg) a different name, if you want to take more than one screenshot.
9. Unmounting is not necessary, if you shut down "GParted" afterwards (nothing stays from your session).
Only in my case, every time I tried the copy action it failed, even though the USB stick was seen and I could browse the folder structure just fine.
Turns out my USB stick was NTFS formatted and GParted couldn’t natively mount and read to that disk format using the regular commands.
In my case, I had to just switch over to a FAT32 formatted USB stick and I could copy to my heart’s content.
I doubt most folks use NTFS on their primary USB drives but I need to due to the size of files that I work with, particularly with imaging, as well as it improves copy performance a bit under WinPE boot work.
Cheers.
--Claus V.












0 comments:
Post a Comment