A quick-post in case others search for a solution for this particular issue:
I’ve been running VMware Player 5.0 on my Windows 7 x64 system for a long while now.
This morning when working in all my Modern.IE Tester VM’s (Win7Ent, Win8 & Win8.1) as well as a fully-installed (and licensed) version of XP Home I noticed the following issues:
- No options showing on VMWare Player tool-bar for three-key toggle, etc.
- Unity working fine however allowing drag/drop of files between host and client desktops.
- After shutting down the running virtualized OS cleanly (Start--shutdown/power-off), the running vm window just stays black and doesn’t close after any length of time.
- Trying to close or force shutdown with the VMware Player options says it is still running and to wait.
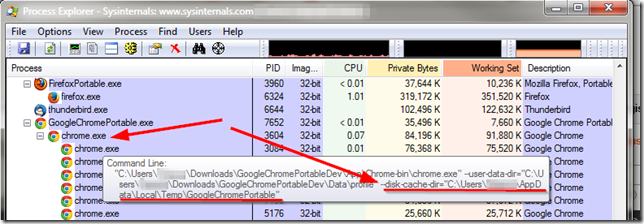
- Checking the running processes showed the sub-process “vmware-unity-helper.exe” still running:
- I was able to kill the process tree to close out the window but that seemed very brutal.
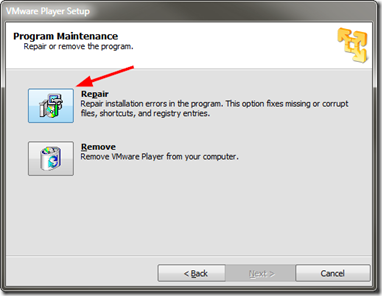
I first tried running a “repair” of VMware Player from the “Programs and Features” options but it would not work as it said the core installation files were missing.
I re-downloaded the VMware Player setup file from VMware and then ran it.
I selected the “repair” option and let it do its thing.
Once finished I relaunched the vm’s and all ran fine, my VMware Player toolbar was restored, and after closing the vm out, after a brief pause, the window closed and the running processes terminated normally.
Not sure what caused the issue but all is well again.
VMware Player “repair” is your friend!
--Claus V.